AWS provides over a hundred plus services which include storage, networking, database, application services, and many more. Out of these services, AWS KMS Key Management Service is a useful and very beneficial service while dealing with sensitive data and it also makes it easy for you to create and manage cryptographic keys.
In this blog, we are going to discuss the overview of AWS KMS, what are its key features, benefits, and much more.
Overview Of AWS KMS
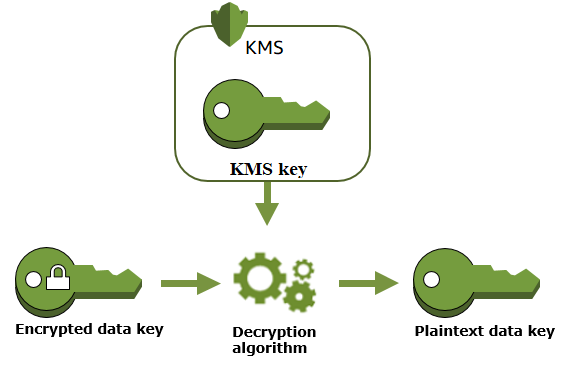
AWS KMS is a safe and resilient service that uses hardware security protocols that are tested or are in the process of being tested to protect our keys. AWS Key Management Service provides a highly available key storage, management, and auditing solution for you to encrypt data within your own applications and control the encryption of stored data across AWS services.

Features of AWS KMS
- It is an easy way to control and access your data using managed encryption.
- With AWS Key Management Service, the process of key management is reduced to a few simple clicks.
- It is also integrated with other AWS services including Amazon EBS, Amazon S3, and Amazon RedShift to simplify the encryption of your data within these services.
- AWS KMS enables you to create, rotate, disable, enable, and define usage policies for master keys and audit their usage.
- It is a centralized key management
- It is secure and compliant.
Why AWS Key Management Service?
Key Management Service is used to encrypt data in AWS. The main purpose of the AWS KMS is to store and manage those encryption keys. Data encryption is vital if you have sensitive data that must not be accessed by unauthorized users. Implement data encryption for both data at rest and data in transit.
Two main methods to implement encryption at rest are Client-Side Encryption and Server Side Encryption.
- Client-Side Encryption where you can encrypt the data at the client-side and send it all the way to the server or any backend services like S3, EBS, Redshift, etc. In short, we can say in client-side encryption you encrypt your data and manage your own keys.
- Server-Side Encryption AWS encrypts the data and manages the keys for you, where you let your backend services to encrypt the data and manage those keys on your behalf.
Advantages of AWS KMS
1. Fully Managed: As you access the encrypted data by assigning permissions to use the keys while AWS Key Management Service deals with the long-lasting and physical security of your keys, hence enforcing your permissions.
2. Centralized Key Management: AWS KMS provides a single point and defines policies continuously across AWS services and also your own applications. By using AWS CLI and SDK or AWS management console you can easily create, rotate, delete, and manage permissions on the keys.
3. Manage Encryption for AWS Service: AWS KMS is integrated with AWS services to simplify the encryption of data. KMS monitors the use of keys to AWS CloudTrail to give you a view of who accessed your encrypted data, including AWS services using them on your behalf.
4. Encrypt Data In your Applications: Using simple APIs you can also build encryption and key management into your own applications wherever they run. Using AWS SDK you can encrypt data locally within your application.
5. Digitally Sign Data: To maintain the integrity of your data, AWS Key Management Service enables you to perform digital signing using asymmetric key pairs.
6. Low Cost: As such there are no charges to use AWS Key Management Service. You are only charged when you use or manage the keys beyond the free tier.
7. Secure: AWS KMS uses hardware security modules that have been validated under FIPS 140-2(Federal Information Processing Standard Publication) or are in the process of being validated, to generate and protect keys. Your keys are only used inside these devices and can never leave them unencrypted. KMS keys are never shared outside the AWS region in which they were created.
8. Compliance: The security and quality controls in AWS KMS have been certified under multiple compliance schemes like AWS KMS is also integrated with AWS CloudTrail for monitoring key usage so that your regulatory and compliance needs are met.
Check out: Amazon Elastic File System (EFS) what it is, its features, how it can be helpful.
Steps to Create Keys Using AWS KMS
- Log in to your AWS account by clicking here
- Open Key Management Service (KMS) Console.

- Service Click on Encryption Keys and click on Create Key.

- The next step is to give the alias or display name to the key and provide a description.

- The next step is to decide who can be given permission to administer the new key by choosing one or more IAM users or roles.

- In the final step, you have to decide which users, roles, and other AWS accounts are allowed to use the key to encrypt and decrypt the data.

Check out: AWS Storage overview and types of storage options offered what are they intended for.
AWS Managed Key Vs. Customer Managed Keys
- AWS Managed Keys can be identified by AWS/service name while Customer manged keys can be given any name.
- AWS Managed Keys are generated by AWS while Customer managed keys are created by customers.
- AWS Managed Keys cannot be deleted while the Customer manged keys can be deleted, enabled and disabled.
- AWS Managed Keys cannot be baked into custom roles while customer manged keys can be baked into custom roles.
- AWS Managed Keys rotate once every three years automatically while the customer-managed keys are rotated once a year automatically or manually.
Security is the top priority and AWS KMS aims to make it as easy as possible for you to use encryption to protect your data above and beyond basic access control. By building and supporting encryption tools that work both on and off the cloud, it helps you secure your data and ensure compliance across your entire environment. AWS KMS puts security at the center of everything that must be done to make sure that you can protect your data that too in a cost-effective way.