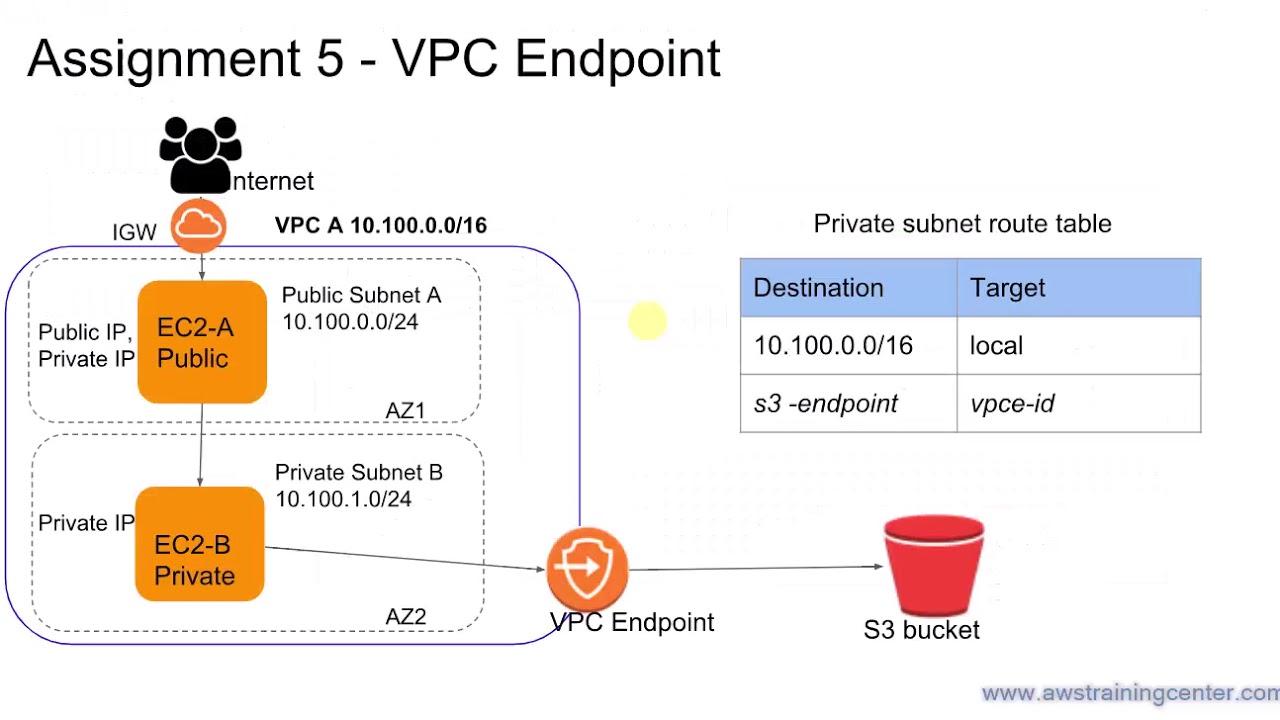
What is VPC endpoint?
VPC Endpoints are a new feature of VPCs (Virtual Private Clouds), a VPC endpoint enables you to privately connect your VPC to supported AWS services and VPC endpoint services powered by PrivateLink using its private IP address, without requiring an internet gateway, NAT device, VPN connection, or AWS Direct Connect connection. Traffic between VPC and AWS service does not leave the Amazon network.

Why is this useful? It means that your network communications no longer have to flow over the public internet to reach the public interfaces of AWS services such as S3, API Gateways; a full list of endpoints can be found below.
For those who face paranoid management types that dislike the use of AWS most powerful features like Cloudwatch and S3 due to their public endpoints (despite the use of SSL). We now have a way to architect a direct and secure data flow!
Type of VPC endpoints
There are two types of VPC endpoints:
Interface endpoint is an elastic network interface (ENI) with a private IP address from the IP address range of user’s subnet that serves as an entry point for traffic destined to a supported service. It enables you to privately access services by using private IP addresses. The following services are supported:
- Amazon CloudWatch Logs
- Amazon EC2 API
- Amazon Kinesis Data Streams
- Amazon SNS
- AWS KMS
- AWS Service Catalog
- AWS Systems Manager
- Elastic Load Balancing API
- Endpoint services hosted by other AWS accounts
- Supported AWS Marketplace partner services
Gateway endpoint is a gateway that you specify as a target for a route in your route table for traffic destined to a supported AWS service. Currently supports S3 and DynamoDB services. The following AWS services are supported:
- Amazon S3
- DynamoDB
VPC Endpoints Key points
- VPC endpoint enables users to privately connect their VPC to supported AWS services.
- VPC Endpoint does not require a public IP address, access over the Internet, NAT device, a VPN connection or AWS Direct Connect to communicate with resources in the service.
- Endpoints are virtual devices, that are horizontally scaled, redundant, and highly available VPC components that allow communication between instances in the VPC.
- Access to the resources in other services can be controlled by endpoint policies.
- By default, Endpoint policy, allows full access to the service. Endpoint policies must be written in JSON format.
- Endpoint policy does not override or replace IAM user policies or service-specific policies (such as S3 bucket policies).
Interface Endpoints:

- When you create an interface endpoint, AWS generate endpoint-specific DNS hostnames (private) that you can use to communicate with the service. This is optional.
- Network ACL for the subnet can restrict traffic, and needs to be configured properly.
Gateway Endpoints:

- A route is automatically added to the Route table with a destination that specifies the prefix list of service and the target with the endpoint id.
e.g. A rule with destination s3 service (pl-63a5400a (com.amazonaws.us-east-1.s3, 54.231.0.0/17, 52.216.0.0/15, 3.5.16.0/21, 3.5.0.0/20)) and a target with this endpoints’ id(e.g. vpce-0b66ba758a38cef8c) will be added to the route tables. - Endpoint needs to be associated with the Route table and the route table cannot be modified to remove the route entry. It can only be deleted by removing the Endpoint association with the Route table or when the endpoint is deleted.
- Security groups needs to be modified to allow Outbound traffic from the VPC to the service that specified in the endpoint. Use the service prefix list ID (e.g. com.amazonaws.us-east-1.s3) as the destination in the outbound rule.
- Multiple endpoints can be created in a single VPC, for multiple services.
- Multiple endpoints to the same service cannot be specified in a single route table.
- You can create multiple endpoints in a single VPC for a single service, But different route tables used to enforce different access policies from different subnets to the same service.
- You can modify the endpoint policy that’s attached to your endpoint, and add or remove the route tables that are used by the endpoint.
VPC Endpoints Limitations
- VPC endpoints support IPv4 traffic only.
- Endpoints are supported within the same Region only. You cannot create an endpoint between a VPC and a service in a different Region.
- Endpoints cannot transfer an endpoint from one VPC to another, or from one service to another.
Interface Endpoints:
- For each interface endpoint, you can choose only one subnet per Availability Zone.
- Each interface endpoint can support a bandwidth of up to 10 Gbps per Availability Zone by default. Additional capacity may be added automatically based on your usage.
- Interface Endpoint supports TCP traffic only.
- Endpoints cannot be transferred from one VPC to another, or from one service to another.
Gateway Endpoints:
- Endpoint connections cannot be extended out of a VPC i.e. resources across the VPN connection, VPC peering connection, AWS Direct Connect connection cannot use the endpoint
Creating an Endpoint
To create an endpoint, open up the AWS management console and head over to your VPC panel, and choose Endpoints:

Create Endpoint Wizard
Click the big blue button, and you should see the following screen, simply select the AWS services you wish to join through this PrivateLink

Routing
Select which routing table and subnets you want routing to the endpoint. In our example we are using the default vpc:

Policies
Permitting a FullAccess policy is impractical to security, we advise utilising the PolicyGenerator to configure a secure policy to prevent any possible data leaks, or future misconfiguration or corruption of data/messages. https://awspolicygen.s3.amazonaws.com/policygen.html
An example policy that restricts access to a particular user in our demo account, and to only S3 API calls:
{
"Version": "2012-10-17",
"Id": "Policy1525026866984",
"Statement": [
{
"Sid": "Stmt1525026861859",
"Effect": "Allow",
"Principal": {
"AWS": "AFIBIMYXS24J9BCCWTTGA"
},
"Action": "s3:*",
"Resource": "arn:aws:s3:::*"
}
]
}
Further Reading
To read up more on Endpoints and PrivateLinks please refer to the AWS documentation available here: https://docs.aws.amazon.com/AmazonVPC/latest/UserGuide/vpc-endpoints.html
For an Overview over advanced VPC design and Endpoints we found this AWS reInvent:2017 talk very useful: https://www.youtube.com/watch?v=Pj11NFXDbLY