As most of the companies and IT professionals look up to containers these days, Kubernetes is the most sought out of all the containers that are available. In this post, we are going to explain about Kubernetes, a.k.a K8s. This is the introduction to our complete Kubernetes guide for beginners, which has more than 25+ articles linked in this.
What is Docker?

In order to understand what is a Docker, a container should be known apriori. As the name suggests a container is a standard unit of software that packages code and all its dependencies so that the application can quickly and also is more reliable.
Docker is a containerization technology that enables the creation and use of Linux containers. It is a tool designed to make it easier to create, deploy, and run applications by using containers. Docker is better than VM in many ways. Here is a comparison of Docker vs Virtual Machines Not only the Linux powers like Red Hat and Canonical have embraced Docker, but the proprietary companies like Microsoft, Amazon, and Oracle have also done it. Know more about Docker Architecture & its components.

Docker Containers v/s Virtual Machine
Docker works on all the platforms. As in how in any container can be created and used on any platform the same way Docker can be installed on different platforms too. A Docker image is a read-only template that contains a set of instructions for creating a container that can run on the Docker platform.
When you start Docker, a default bridge network (also called a bridge) is created automatically, and newly-started containers connect to it unless otherwise specified. You can also create user-defined custom bridge networks. Know more about Docker Networking
What is Kubernetes

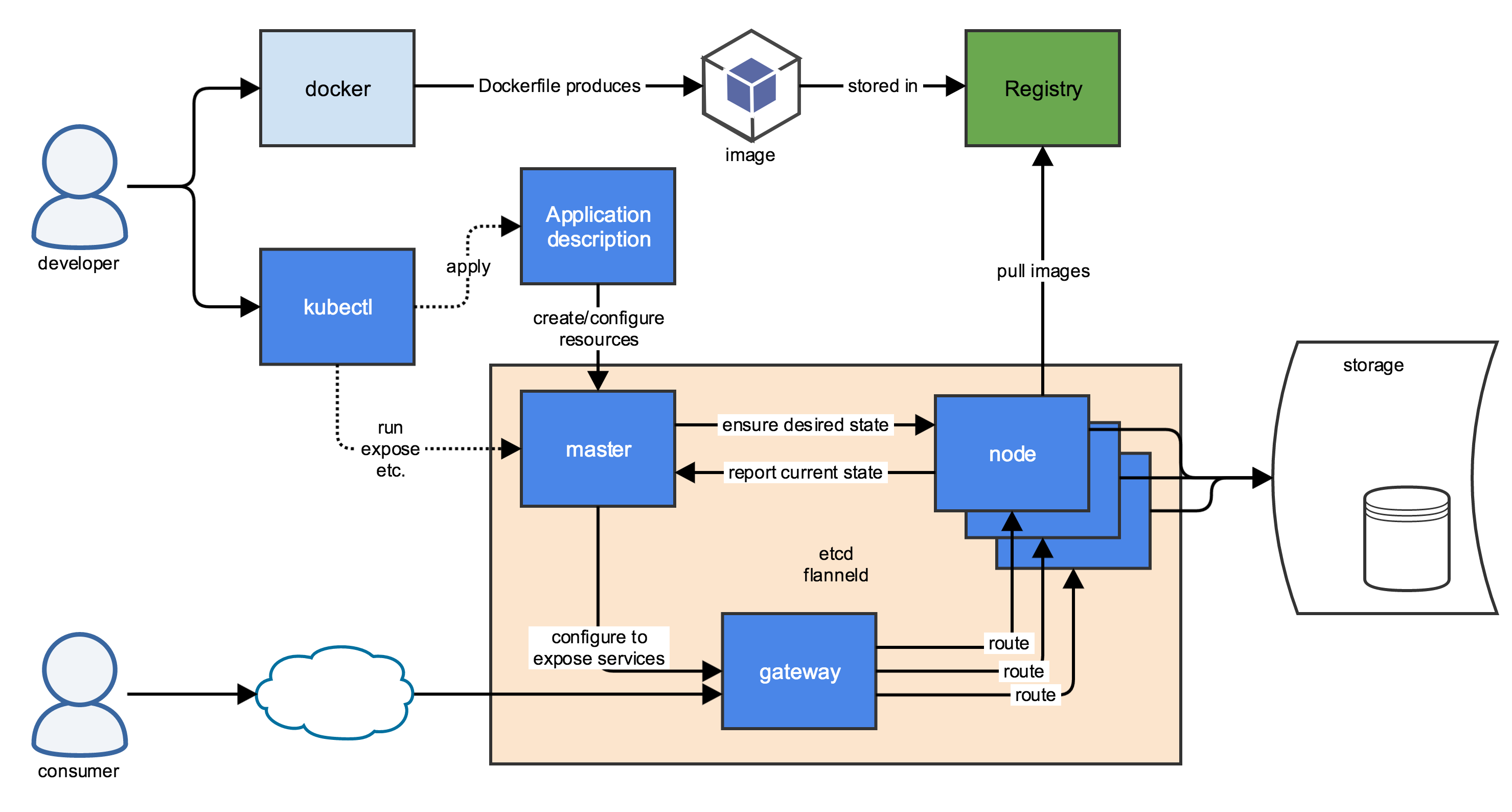
“Kubernetes” is a Greek word, which means helmsman or pilot which also gives us an idea of how the logo was made. Now, let us come to the technical part of it since Docker has its own limitations, Kubernetes comes into the picture to fill the gaps in the Docker containerization process. K8s is a complete containerization orchestration, which provides the ability to run dynamically scaling, containerized applications, and utilizing an API for management. By doing a comparison of Docker & Kubernetes one can deduce the advantages of Kubernetes over other containerization orchestration.

The architecture of Kubernetes is so simple, it consists of Master nodes and Worker nodes, the Master communicates with the Worker using API-server. Multiple Master nodes may also exist in order to provide High Availability, which is indeed one of the most important aspects of application deployment and also an advantage of Kubernetes.
Know more about Kubernetes vs Docker
K8s has a lot of advantages, we will shed some light on it later. The packaged application can be managed Helm and Helm Charts which is one of the most important parts of packaging an application. Now let us look at the basic components of Kubernetes…
Also read: How to install docker on Windows, Ubuntu and MAC
Kubernetes Objects
Before one wants to work on K8s, they should know about the basic components in Kubernetes and also about objects in API. Basic objects and several higher-level abstractions are known as controllers. These are the building block of the application lifecycle.
Basic objects include:
- Pod. A group of one or more containers, a simple deployable unit of K8S.
- Service. An abstraction that defines a logical set of pods as well as the policy for accessing them.
- Volume. An abstraction that lets us persist data. This is necessary because containers are ephemeral—meaning data is deleted when the container is deleted.
- Namespace. A segment of the cluster dedicated to a certain purpose, for example, a certain project or team of devs.
Controllers, (higher-level abstractions) include:
- ReplicaSet (RS). Ensures the desired amount of pod is what’s running.
- Deployment. Offers declarative updates for pods an RS.
- StatefulSet. A workload API object that manages stateful applications, such as databases.
- DaemonSet. Ensures that all or some worker nodes run a copy of a pod. This is useful for daemon applications like Fluentd.
- Job. Creates one or more pods, runs a certain task(s) to completion, then deletes the pod(s).
Now, let us look at some of them:
Microservice
Monolithics had way too many backlogs, this is why Microservices have come into the picture. A traditional micro-service based architecture that would have multiple services making up one, or more, end products. Microservices are typically shared between applications and make the task of CI/CD easier for management.
Learn more about Microservices.
Images
Typically a docker container image – an executable image containing everything you need to run your application; application code, libraries, runtime, environment variables, and configuration files. At runtime, a container image becomes a container that runs everything that is packaged into that image.
Learn more about Docker Images.
Labels and Annotations
Labels and Annotations in Kubernetes are one of the main components. They both provide a way for adding additional metadata to our Kubernetes Objects but there one difference between them. Labels allow us to do a grouping of our objects so that we can perform queries for viewing and operating while Annotations are used for adding non-identifying metadata to Kubernetes objects.
Learn more about Labels and Annotations.
Pods
A single or group of containers that share storage and network with a K8s configuration, telling those containers how to behave. Pods share IP and port address space and can communicate with each other over localhost networking. Each pod is assigned an IP address on which it can be accessed by other pods within a cluster. Applications within a pod have access to shared volumes – helpful for when you need data to persist beyond the lifetime of a pod.

Learn more about Kubernetes Pods.
Namespaces
Namespaces are a way to create multiple virtual K8s clusters within a single cluster. Namespaces are normally used for wide-scale deployments where there are many users, teams, and projects.

Replica Set
A Kubernetes replica set ensures that the specified number of pods in a replica set is running at all times.

A Replica Set allows you to define the number of pods that need to be running at all times and this number could be “1”. If a pod crashes, it will be recreated to get back to the desired state. For this reason, replica sets are preferred over a naked pod because they provide some high availability.
Deployments
A way to define the desired state of pods or a replica set. Deployments are used to define HA policies to your containers by defining policies around how many of each container must be running at any one time.

In Kubernetes, most service style applications use Deployments to run applications on Kubernetes. Using Deployments, you can describe how to run your application container as a Pod in Kubernetes and how many replicas of the application to run. Kubernetes will then take care of running as many replicas as specified.
To know more about Kubernetes Networking, Click here
Services
Coupling of a set of pods to a policy by which to access them. Services are used to expose containerized applications to origins from outside the cluster.

Service is both an abstraction that defines a logical set of pods and a policy for accessing the pod set. There are 4 types of services viz. NodePort. ClusterIP, LoadBalancer and ExternalName.
Also Read: Our blog post on Kubernetes Monitoring. Click here
Nodes
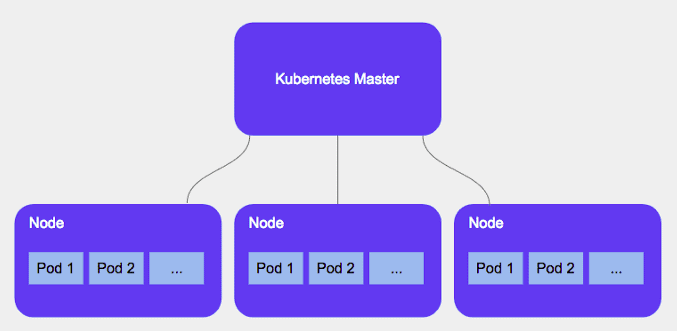
Kubernetes run your workload by placing containers into Pods to run on Nodes. A node may be a virtual or physical machine, depending on the cluster.

A Node is a worker machine and may be either a virtual or a physical machine, depending on the cluster. Each Node is managed by the Master. A Node can have multiple pods. So it’s a one to many relationship. The Kubernetes master automatically handles scheduling the pods across the Nodes in the cluster
Cluster
A Kubernetes Cluster is a group of node or machines running together. It consists of two types of servers, a Master Node and a Worker Node. These servers can be Virtual Machine(VM) or physical servers(Bare metal). Together, these servers form a Kubernetes cluster and are controlled by the services that make up the Control Plane.
Get all the steps to create a 3 Node Cluster.
If you want to know how to create an AKS Cluster, you can check our blog on Create AKS Cluster: A Complete Step-by-Step Guide
Kubernetes Security

Kubernetes security is important throughout the container lifecycle due to the distributed, dynamic nature of a Kubernetes cluster. Kubernetes offers a rich set of controls that can be used to effectively secure clusters and their applications. Different security approaches are required for each of the three phases of an application lifecycle: build, deploy, and runtime.
Network Policies

One important configuration that demands attention from a security perspective is the network policy feature. This is Kubernetes assets that control the traffic between pods. Kubernetes network policy lets developers secure access to and from their applications. This is how we can restrict a user for access.
Learn more about Network Policies
RBAC – Role-Based Access Control

It is a technique of regulating access to a computer or network resources based on the roles of individual users within an enterprise. In this context, access is the ability of a private user to perform a selected task, like read, create, or modify a file.
Learn more about Role-Based Access Control
Kubernetes Benefits
On a bigger note, it is very easy to see why has K8S become so popular, it is a flexible and scalable and also an open-source container orchestration. But what are the benefits that really matter to the companies? Well, here is why:
- Control and automate deployments and updates
- Save money by optimizing infrastructural resources thanks to the more efficient use of hardware
- Orchestrate containers on multiple hosts
- Solve many common problems deriving by the proliferation of containers by organizing them in “pods”
- Scale resources and applications in real-time
- Test and autocorrection of applications
Kubernetes Certification
The Cloud Native Computing Foundation (CNCF), along with the Linux Foundation together, has created certification programs for K8s which most of the professionals are looking to add on to their skill-set. They are respectively:

Certified Kubernetes Administrator (CKA): This certification provides assurance that a CKA has the skills, knowledge, to perform the responsibilities of Kubernetes administrators. This certification is for Kubernetes administrators, cloud administrators, and other IT professionals who manage Kubernetes instances.
Certified Kubernetes Application Developer (CKAD): This certification is designed to guarantee that certification holders have the knowledge, skills, and capability to design, configure, and expose cloud-native applications for Kubernetes and also perform the responsibilities of Kubernetes application developers.
Certified Kubernetes Security Specialist (CKS): This program will consist of a performance-based certification exam and assures that a CKS has the skills, knowledge, and competence on a broad range of best practices for securing container-based applications and Kubernetes platforms during build, deployment, and runtime.
Step-by-Step Activity Guides (Hands-on Labs)
In order to clear the Kubernetes Certifications, all you need is practical knowledge, this comes only by practicing. Below is the list of our complete activity guides which are hands-on labs for acing these exams:
- Hands-on labs for Certified Kubernetes Administrator (CKA): Step-by-Step Activity Guide
- Activity guide for Certified Kubernetes Application Developer [CKAD]
- Hands-on labs for Certified Kubernetes Security Specialist [CKS]: Step-by-Step Activity Guide
Kubernetes on Cloud (Managed Kubernetes)
K8s is very hard to be managed on its own so, managed Kubernetes has become an important strategy for companies seeking to monetize K8s.
Managed Kubernetes is when third-party providers take over responsibility for some or all of the work necessary for the successful set-up and operation of K8s. Depending on the vendor, “managed” can refer to anything from dedicated support, to hosting with pre-configured environments, to full hosting and operation.
Azure Kubernetes Service by Microsoft (AKS)

Azure Kubernetes Service (AKS) is a fully-managed service that allows you to run Kubernetes in Azure without having to manage your own Kubernetes clusters. Azure manages all the complex parts of running Kubernetes, and you can focus on your containers. AKS is one of the pioneers of managed Kubernetes service
Elastic Kubernetes Service by Amazon (EKS)

Amazon EKS is a managed service that helps make it easier to run Kubernetes on AWS. Through EKS, organizations can run Kubernetes without installing and operating a Kubernetes control plane or worker nodes. Simply put, EKS is a managed containers-as-a-service (CaaS) that drastically simplifies K8s deployment on AWS.
Know more about Elastic Kubernetes Service and how to create a cluster and also other benefits of AKS.
Oracle Kubernetes Engine by Oracle Cloud (OKE)

The Oracle Container Engine for Kubernetes (OKE) is a hosted Kubernetes cluster (IAAS – Infrastructure As A Service) provided by Oracle and highly integrated with other Oracle Cloud offerings. Oracle Cloud Infrastructure Container Engine for K8s is a fully-managed, scalable, and highly available service that you can use to deploy your containerized applications to the cloud. To know more about Oracle Container Engine for Kubernetes (OKE), click here.
Google Kubernetes Engine by Google Cloud (GKE)

The Google Kubernetes Engine (GKE) is a hosted Kubernetes cluster (IAAS – Infrastructure As A Service) provided by Google. The Google Kubernetes Engine (GKE) is a fully managed Kubernetes service for deploying, managing and scaling containerized applications on Google Cloud. The GKE environment consists of multiple machines (specifically, Compute Engine instances) grouped together to form a cluster. To know more about Google Kubernetes Engine (GKE), click here.
K8s for Different Professionals

In today’s IT world, the scale and complexity of projects are increasing exponentially. K8s counters this by automatically scaling and managing containers that are used to deploy and test project or application modules. There is a huge gap in the IT Job market and also with a higher salary for a Certified professional, here are some of the examples:
- Kubernetes will be the most important skill for a DevOps professional.
- To be ahead of all, its high time for Testers & QA professionals to learn K8s.
- Kubernetes already is and going to be the most important tool for developers since all the applications will be containerized in the future.
- The System Administrator will require to have K8s skill very soon.
- Professionals with a bit of Linux knowledge having K8s knowledge will yield them the best results.